Looks like the door unlock fob that you have on your keychain that uses can probably be cracked in about an hour. Many car manufactures such as GM, Toyota, VW, Fiat, Chrysler, Daewoo, Honda, Jaguar, and Volvo are at risk!
“A group of Israeli and Belgian researchers found a vulnerability in the algorithm that is used to secure anti-theft digital key systems in numerous vehicles, including those made by such companies as Honda, Ford, General Motors, Mercedes Benz and Jaguar. With that information they were able to devise an attack to crack the code of anti-theft keys.”
Via: I Hacked
KeeLoq Remote Vehicle Entry System Cracked

Permalink
It takes a day to crack the first code for a car model, then just seconds to crack additional codes for that model.
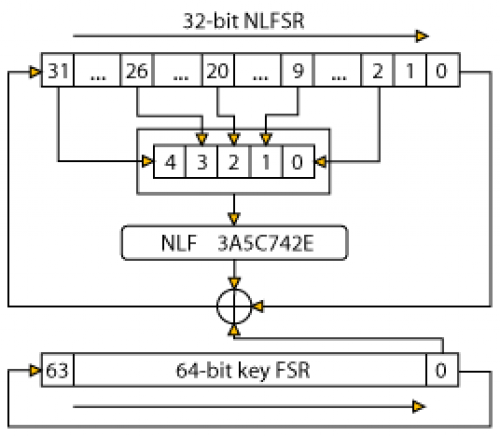
“The attack involves probing a digital key wirelessly by sending 65,000 challenge/response queries to it. Once the researchers collect 65,000 responses – which takes about an hour – they use software they designed to decipher that key’s unique code. [b]The deciphering currently takes about a day[/b] using a dedicated computer. But once they’ve cracked one key, they know 36 bits of the 64 bits they need to know. Those 36 bits are identical for every car model a manufacturer makes (different car models will vary only slightly).”
“This doesn’t mean Dunkelman can just walk onto a parking lot and open any car that’s the same model of the one he cracked. He still needs to crack the unique key used to open the other cars. But because he already knows the 36 bits that are common to all of the keys for one model of car, [b]it takes only a few seconds to crack those other keys[/b].”
Permalink
It uses rolling encryption and a 2 challenge limit, thus after 3 wrong hits it invalidates the synchronized key.
It is not Microchip’s fault if the car company was too stupid to implement the system correctly.
Whoever left the main host open to a primate level brute force attack deserves a banana…